OpsCenter has successfully met the information security standards of every organization that has installed it. This includes very knowledgeable, security-oriented organizations in the Fortune 100 and highly classified military systems. Alert Technologies consultants will be able to assist your staff members in achieving an equally high degree of information security with OpsCenter.
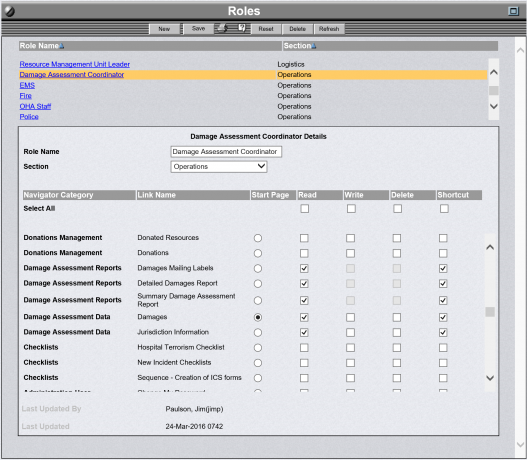
OpsCenter Roles Administration Screen
OpsCenter Information Security
OpsCenter incorporates multiple Information Security designs. For example, OpsCenter maintains its own security layer that controls access according to the different roles configured into the system. This allows an organization to establish a role such as Purchasing Officer and set related permissions. The role-based security allows an organization to give a particular type of user only the minimum authorizations required.
To authorize the Purchasing Officer to access or modify emergency procurement information an Administrator simply makes the appropriate selections on the Role Administration Screen. The ease of use built into OpsCenter allows an authorized non-technical user to make these changes.
Each user must be authorized to perform at least one role and may have more. The Users Administration Screen is used to specify which role(s) a user is authorized to perform. When a user logs onto OpsCenter, they must choose which roles they will fulfill from their authorized list. The user then inherits the permissions designated for those role(s). OpsCenter User ID's have no permissions; they get all permissions from their role(s).
The role-based security is a layer of security enforced on top of the security at the web server level, the database level, and the operating system level. For example, OpsCenter may be installed on a web server that is running Secure Socket Layer (SSL) or is running on special ports. This provides strong over-the-wire encryption of information via the Secure Socket Layer (SSL).
Another security technique that can be used with OpsCenter is to authenticate every file access (*.htm, *.ASP, etc.) using operating system security mechanisms. With this approach every single file access is authenticated.